
Neural Efficiency for a Transparent Transactions Ecosystem
whitepaper
- Version: 1.1.3
- Author: the nette ecosystem team
- Create: 21 Sep 2023
- Update: 05 Dec, 2024
This paper highlights Paynette's multi-chain and modular payment features, the Tradenette pooled deep trading platform, and the Coinette token, a crypto asset designed to support and strengthen the entire Nette Ecosystem. Additional ecosystem content will be included in future updates.
important considerations before reading:- Licenses and Approvals: While the Nette team is committed to complying with all applicable laws and regulations in both domestic and international markets, obtaining the necessary licenses and approvals cannot be guaranteed. We will endeavor to secure the required authorizations to operate legally and efficiently.
- Regulatory Limitations: Licenses and regulatory approvals may vary by jurisdiction and can include specific restrictions. As a result, the development and expansion of the initiatives outlined in this white paper may be subject to conditions and are not guaranteed.
- No Guaranteed Timeline: There is no assurance that the necessary licenses or approvals will be obtained within a specific timeframe. Consequently, the initiatives discussed in this white paper may be restricted or unavailable in certain jurisdictions.
- Third-Party Collaborations: The development process may involve partnerships with licensed third parties, which could necessitate adjustments to the structure of our plans or modifications to certain services, including their potential unavailability. If any third parties lose their regulatory licenses, it may impact Nette's ability to rely on their services and could lead to the termination of such collaborations.
- External Content Disclaimer: Content found on other websites, visual or audio media, and social media platforms not directly associated with this white paper does not represent the official views or endorsement of Nette.
- Security Reminder: This content is freely accessible, and we will never ask for your private key, password, or one-time password.
- Independent Operation: Nette is not affiliated with or owned by any other media outlet, website, or commercial entity outside of those mentioned in this white paper.
disclaimer
- This whitepaper does not constitute investment, financial, business advice, or a recommendation from Nette or its affiliated teams, brands, employees, directors, agents, or advisors to purchase Coinette Tokens.
- Coinette Tokens do not represent a share in Nette or any affiliated brands. Instead, they are a digital asset (token) originally issued by Tradenette to raise capital for future projects. Token holders retain full ownership of their tokens as long as they hold them.
- This document is not a prospectus or financial services offering and does not constitute an invitation to buy or sell securities, investment products, regulated products, or financial instruments within any jurisdiction. Coinette Tokens are not classified as securities or structured tokens in relation to Nette or its affiliates. Ownership of Coinette Tokens does not entitle holders to equity, royalties, profits, or income from Nette or affiliated entities.
- No warranties or guarantees are made regarding the accuracy, completeness, or reliability of the information presented in this whitepaper, including any omissions from previous versions.
- Coinette Tokens are still under development and may be subject to updates that differ significantly from the descriptions in this whitepaper. No warranties are provided regarding the availability, reasonableness, or future viability of the programs and services outlined, nor should anything in this document be interpreted as a guarantee or forecast.
- Nette accepts no liability for any loss or damage (foreseeable or not) arising from the use of this whitepaper or its content. The information provided herein does not represent negligence, omission, or the failure to meet obligations.
- Data from third-party sources has not been independently audited or verified by legal, financial, or technical experts, and no assurances are provided regarding its accuracy or completeness.
- This whitepaper must not be distributed or published in jurisdictions where such actions are restricted or prohibited by regulatory authorities.
- The views expressed in this whitepaper are those of Nette and do not reflect the official stance of any government, public body, or regulatory authority. This whitepaper has not been independently reviewed or endorsed by any regulatory agency.
- Coinette Tokens must not be purchased for speculative investment, illicit activities, or any illegal trade or service purposes. Token holders should only purchase Coinette Tokens if they fully understand the risks involved with cryptocurrencies.
risks
- Purchasing Crypo Tokens involves risk and could result in significant financial loss. Before purchasing (including coinette tokens), potential buyers should carefully evaluate the associated risks.
- Crypto tokens are susceptible to theft or expropriation. Hackers or malicious entities, including unauthorized organizations or governments, could target our network through methods such as malware, denial-of-service attacks, consensus manipulation, or spoofing, potentially leading to token loss. In such cases, there may be no recourse or compensation for affected holders.
- The regulatory environment for crypto tokens and digital assets remains uncertain and varies globally, potentially subjecting future operations to regulations or laws that could impact token holders' rights. Tax regulations concerning crypto tokens are also unclear, potentially exposing holders to unforeseen tax obligations.
Potential buyers are advised to consider all the risks and pitfalls of the cryptocurrency market and consult with experienced and trusted advisors before making an investment decision.
idioms and phrases
- The Nette Ecosystem is a service-oriented, vertically scalable, performance-driven, and dynamic neural chain ecosystem powered by artificial intelligence, launched in 2019. The word "Nette" means clear and pure. All services within this ecosystem incorporate "nette" in their names, such as tradenette™, paynette™, and coinette™.
- paynette™ is a trademark representing an efficient, ultra-fast, decentralized, and encrypted multi-chain network within the Nette Ecosystem. It supports payments, transactions, financial processes, and money transfers (both crypto and fiat). Its integrated and scalable structure accelerates financial management and ensures seamless operations.
- Initially tradenette™ was an AI-based cryptocurrency market analysis engine built on the ALICE model. Today, it functions as an intelligent trading platform for investment modeling, low-risk trading, valuation, and risk management. tradenette™ also serves as the research core for other Nette Ecosystem teams and subsidiaries.
- coinette™ is a cryptographic utility token designed to bolster investment pools and provide initial capital for developing the tradenette™ infrastructure. It now serves as a critical support system for the entire Nette Ecosystem.
- ALICE™ stands for Algorithmic Lightweight Intelligent Catalyze Engine. Far from being a personal name, ALICE is an advanced artificial intelligence deep algorithm (AIDA) developed by tradenette™. It analyzes irrational cryptocurrency market behaviors with over 3.96 million concurrent samplings per token, identifying optimal trading points.
- FIONA™ stands for Fast Input & Output of Network Arrays. It is a competitive, array-oriented, decentralized, and dynamic architecture developed by Nette. Based on neural array behaviors, FIONA powers the dPAP network, enhancing blockchain network capabilities. Each processing node dynamically generates its template based on the requested service, enabling seamless data transfer across inter-blockchains.
- dPAP stands for Decentralized Payment Aggregator Protocol. Built on FIONA™, it aggregates data from multiple blockchains into a unified decentralized protocol. This allows customers to transact seamlessly across blockchains, regardless of the currency type or conversion ratios, delivering a fast and user-friendly experience.
the goal
The Nette Ecosystem seeks to transform the financial landscape by constructing an efficient, ultra-fast, decentralized, and encrypted multi-chain network that seamlessly integrates a variety of financial services. This innovative infrastructure is designed to enhance payments, transactions, financial management, and money transfers, accommodating both fiat and digital currencies. By incorporating advanced artificial intelligence and virtual pools, the Nette Ecosystem aims to create an intelligent, adaptable financial platform for users of all kinds.
The core of the Nette Ecosystem is built around virtual pools, a revolutionary approach to liquidity management that sets a new standard in decentralized finance. These pools provide users with the ability to pool resources for optimal returns, dynamic asset allocation, and sophisticated financial strategies. By enabling efficient resource distribution, advanced liquidity management, and integrated global investments, virtual pools ensure users can maximize their financial potential with ease and precision.
Leveraging AI-powered algorithms, these virtual pools are designed to enhance performance, minimize transaction costs, and support automated, real-time decision-making for both individual users and businesses. This AI-driven optimization continuously assesses market conditions, adapts to fluctuations, and identifies opportunities to achieve optimal asset management.
The integration of AI and virtual pools within the Nette Ecosystem not only streamlines operations but also unlocks significant profitability and convenience. Users can benefit from automated investment strategies, seamless transactions, and reduced costs, elevating their experience and positioning Nette as a leader in the future of decentralized finance. This innovative approach empowers participants to achieve higher efficiency and improved financial outcomes, reshaping the landscape of global investments and liquidity management.
decentralized payment aggregator protocol
Since 2013, the competition to improve blockchain scalability, security, and transaction speed has intensified within the crypto markets. Equally important is the development of networks or protocols that enable seamless communication between blockchains. However, businesses relying on crypto payment gateways still face challenges that hinder widespread daily use of cryptocurrencies.
The Decentralized Payment Aggregator Protocol (DPAP) addresses these challenges by leveraging advanced algorithms and artificial intelligence within the Nette Ecosystem. DPAP aggregates data from multiple blockchains into a unified, decentralized protocol, enabling transactions across diverse blockchain networks, currencies, and conversion rates.
Beyond basic transaction processing, DPAP performs advanced functions such as linking liquidity pools, reducing transaction fees, and facilitating fund transfers to and from DeFi pools. Its AI-driven solutions ensure efficiency and reliability for businesses and consumers alike.
Key Advantages of DPAP in the Nette Ecosystem:
- Faster, Safer, and More Scalable Transactions: Harnessing cutting-edge AI algorithms, DPAP optimizes transaction speed and security across networks, overcoming traditional blockchain limitations.
- Automated Receipt, Exchange, and Payment Processes: AI-powered automation simplifies complex workflows, enabling seamless receipt, exchange, and payment operations across traditional and blockchain-based systems.
- Decentralized Inter-Network Protocol: A robust protocol bridges traditional banking systems with blockchain networks, allowing effortless currency exchanges between fiat and digital currencies.
- Significant Cost Reductions: By minimizing transaction fees by up to 70%, DPAP offers substantial cost savings for businesses and users, encouraging broader adoption of crypto payments.
- Integrated and AI-Driven Customer Interactions: Intuitive, AI-enhanced interfaces provide users with a seamless, user-friendly experience, fostering trust and reliability in crypto payment solutions.
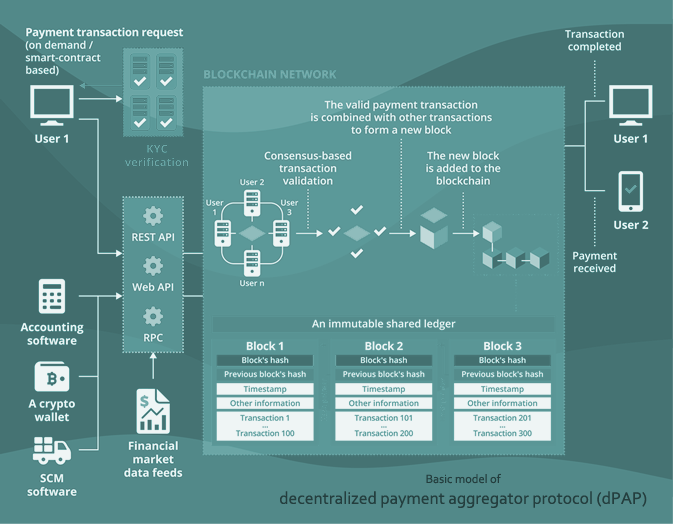
The Nette Ecosystem, powered by its Decentralized Payment Aggregator Protocol, redefines crypto payments with innovation, intelligence, and efficiency, enabling businesses and users to thrive in a connected, decentralized financial world.
tradenette™
your gateway to smart investment
Tradenette is a pioneering platform that empowers users to harness the potential of financial markets through innovative trading and investment tools. It seamlessly integrates advanced technology and blockchain to offer users access to a diverse range of assets, making trading smarter, faster, and more accessible than ever.
Key Features of Tradenette:
- Integrated Financial Gateway: Connect your Paynette wallet to execute trades or make withdrawals without conversion fees.
- Advanced Asset Diversity: Trade in a wide array of assets, including cryptocurrencies, tokenized real estate, precious metals, commodities, and more.
- QUI Token Utility: Use Coinette (QUI) to access reduced fees, staking rewards, and exclusive platform features, ensuring that your investments work smarter for you.
- Pooled Investment Opportunities: Participate in large-scale investments by pooling resources with other users. From real estate to venture capital, Tradenette democratizes high-value opportunities.
- AI-Powered Insights: Utilize artificial intelligence and machine learning to receive real-time analytics, predictive insights, and algorithmic strategies for optimal decision-making.
- Customizable Investment Models:
Tailor your investments with flexible payment structures, including:
- Per transaction or portfolio creation.
- Per performance milestone.
- Subscription-based models for managed portfolios.
- Secure and Transparent Trading:
- Benefit from peer-to-peer encryption and immutable blockchain technology.
- Tradenette ensures end-to-end transparency for every transaction and trade.
- Cost-Efficient Cross-Border Investments: Facilitate international transactions and investments with reduced fees, eliminating intermediaries, and accelerating transaction speed.
- Integration with Paynette: Trade and invest seamlessly with Paynette for instant deposits, withdrawals, and currency exchanges across fiat and crypto.
paynette™
the ultimate payment solution
Paynette redefines the payment experience by seamlessly bridging the gap between traditional banking systems and cryptocurrency wallets. Imagine having the power to connect your bank account, Visa, or Mastercard directly to your crypto wallet, enabling full control of your money for use at any point of sale, ATM, cash register, or electronic payment terminal—without the hassle of currency conversion. Paynette transforms how individuals and businesses transact, offering cutting-edge features and unmatched convenience.
Key Features of Paynette:
- No Setup Fee and No Minimum Balance: Get started instantly without any upfront costs or obligations.
- Domestic Transaction Fee: 0% Enjoy fast and seamless peer-to-peer payments, perfect for retail, healthcare, public transportation, entertainment, hospitality, and other industries. Paynette supports QR code-based, NFC-based, and biometric-based payments for secure and contactless in-person transactions.
- Contactless and Biometric Payments: Leverage the latest payment technologies for speed and security in every transaction.
- Deposit and Withdrawal Without Fees: Transfer funds to and from your Tradenette™ account without incurring fees, simplifying your financial activities.
- Cross-Border Payments Made Easy: Benefit from cost-effective, fast, and transparent international transactions without intermediaries. Gain complete end-to-end visibility of your payments to enhance financial control.
- Autonomous Dedicated Ledger: Nette's blockchain technology ensures tamper-resistant records, full traceability, and immutable data for secure and reliable transactions.
- Advanced Customization for Payments:
Tailor your payment methods to suit your business model:
- Per product, download, or visit.
- Per registration, membership, or subscription.
- For streaming music, video, or other online content.
- Government Payment Automation: Automate tax payments and other government transactions to avoid late penalties, reduce fraud, and ensure compliance with jurisdictional regulations.
- Peer-to-Peer Encryption and Gateway Connectivity:
- Connect multiple wallets to a single gateway or vice versa.
- Enable automatic currency exchange between sender and receiver for smooth global transactions.
- Diverse Payment Acceptance: Businesses can accept Bitcoin, altcoins, stablecoins, or fiat currencies with Paynette, enhancing accessibility and flexibility.
payment as a service
Payments as a Service (PaaS) is a modern approach to simplifying and enhancing the payment ecosystem by offering an integrated solution to connect multiple payment systems seamlessly. On the Nette ecosystem, PaaS takes this concept further, leveraging cutting-edge blockchain technology and smart integrations to address the complexities of the evolving global financial landscape.
Revolutionizing the Payment Ecosystem
The global shift towards digital payments, open banking, and digital wallets, alongside the decline in cash usage, is transforming the payments landscape. However, this transformation presents challenges such as:
- Regulatory compliance
- Risk management
- Transaction fraud prevention
To meet these demands, businesses need a flexible and scalable solution. By adopting a Payments as a Service model, organizations can reimagine their payment infrastructure as a managed service, eliminating inefficiencies and unlocking new opportunities for growth.
Why Choose PaaS on the Nette Ecosystem?
The Nette ecosystem introduces a blockchain-enhanced PaaS solution designed to:
- Accelerate Business Growth: Focus on scaling your business without the complexities of traditional payment processes. The Nette PaaS handles integration, compliance, and updates, empowering you to expand without barriers.
- Enhance Financial Transparency: Gain real-time insights into your company's financial operations. The Nette PaaS provides detailed dashboards and analytics, enabling informed decision-making at every step.
- Optimize Cost Management: Predictability is crucial for financial success. The Nette PaaS equips you with tools to forecast, manage, and control costs effectively, avoiding unexpected expenses.
- Streamline Operations: Transition to the digital age by automating and optimizing payment workflows. Say goodbye to manual, time-consuming tasks and focus on achieving core business objectives.
- Eliminate Hidden Fees: Unlike traditional payment methods, the Nette PaaS is transparent and cost-effective, helping you save resources and allocate funds strategically.
Key Features of Nette PaaS
- Blockchain-Driven Architecture: Harness the power of blockchain for immutable records, end-to-end encryption, and streamlined cross-border transactions.
- Customizable Payment Methods: Support tailored payment structures such as per subscription, per transaction, or dynamic pricing models based on user requirements.
- Integrated Ecosystem: Seamlessly connect with other Nette ecosystem services like Tradenette and Paynette for a unified financial experience.
- Efficient Infrastructure Management: Nette PaaS handles servers, storage, networks, virtualization, middleware, operating systems, and runtime. Businesses only need to focus on providing data and applications.
Unlocking Savings and Simplification
With no need to purchase hardware or worry about downtime, the Nette PaaS offers significant cost savings. By outsourcing payment technology management, businesses can:
- Reduce operational costs
- Improve system reliability
- Avoid disruptions caused by maintenance or upgrades
The Future of Payments with Nette PaaS
By adopting the Payments as a Service model on the Nette ecosystem, businesses gain a competitive edge in today's fast-paced financial environment. This innovative approach not only simplifies payment processing but also empowers organizations to achieve growth, transparency, and efficiency on a global scale.
the nette payment service provider (NPSP)
The Payment Service Provider (PSP) is an integral component of the Nette ecosystem, designed to streamline and elevate the payment experience for businesses and users. By leveraging the power of blockchain technology and the interconnected services within the Nette ecosystem, the PSP ensures secure, efficient, and flexible payment processing tailored to modern financial needs.
what is a PSP in the nette ecosystem?
A PSP acts as a bridge between businesses, consumers, and financial institutions, enabling seamless transaction processing across various payment methods. Within the Nette ecosystem, the PSP integrates advanced blockchain protocols, eliminating inefficiencies, reducing costs, and enhancing transparency.
Key Features of the Nette PSP
- Comprehensive Payment Options
- Supports cryptocurrencies, stablecoins, and fiat currencies.
- Enables peer-to-peer payments, cross-border transactions, and traditional payment methods such as credit cards and bank transfers.
- Facilitates payments through modern technologies like QR codes, NFC, and biometric authentication.
- Blockchain-Powered Security
- End-to-end encryption ensures data integrity and user privacy.
- Immutable transaction records provide transparency and accountability.
- Autonomous smart contracts automate payment execution, reducing human error and fraud risks.
- Global Accessibility
- Enables businesses to accept payments from anywhere in the world.
- Cost-effective international transactions without intermediaries.
- Real-time currency conversion for cross-border transactions.
- Integration with Nette Services
- Seamless connectivity with Tradenette for investment and trading needs.
- Direct linkage with Paynette for everyday financial operations, including point-of-sale, ATM access, and online transactions.
- Unified user accounts across the ecosystem for effortless management.
- Enhanced User Experience
- No setup fees and no minimum balance requirements.
- Zero domestic transaction fees for in-network payments.
- Fast and convenient payment processing for retail, healthcare, hospitality, and more.
- Customizable Solutions for Businesses
- Tailored payment models: per product, per subscription, per visit, or per download.
- Dedicated dashboards for financial reporting and analytics.
- Automated tax and compliance handling to reduce administrative burdens.
Why Choose the Nette PSP?
- Cost Efficiency: Businesses save on hidden fees and intermediaries while benefiting from predictable cost structures.
- Scalability: The PSP is built to handle transactions of any size, making it suitable for small businesses and large enterprises alike.
- Interoperability: Integration with multiple wallets and gateways allows businesses to provide flexible payment options to their customers.
- Future-Ready Payments: Embracing blockchain technology ensures the PSP evolves with market trends, regulatory changes, and user expectations.
Use Cases for the Nette PSP
- Retail: Accept payments online and in-store with ease.
- Healthcare: Enable secure transactions for medical services and insurance claims.
- Hospitality: Provide contactless payment options for hotels, restaurants, and travel services.
- Government: Streamline tax payments, fines, and other transactions with automated systems.
A Unified Ecosystem for Payments
The Nette PSP is more than just a payment processor, it's the cornerstone of a connected financial ecosystem. By aligning with the broader goals of the Nette ecosystem, it empowers businesses and individuals to transact with confidence, efficiency, and transparency.
With its robust features and seamless integration into the Nette ecosystem, the PSP redefines the standard for payment service providers, making it a vital tool for any forward-thinking organization.
pci dss
The payment card industry data security standard, or PCI DSS, is required for those managing cardholder information, whether a start-up or an international company. All payment gateways must be compliant at all times, and compliance must be reviewed and verified annually.
The PCI Standards Council (SSC) is responsible for developing PCI compliance standards. It aims to help secure and protect the entire payment card ecosystem. These standards apply to merchants and service providers who process credit or debit card payment transactions.
PCI Compliance
Payment Card Industry Compliance (PCI) is required by credit card companies to help ensure the security of credit card transactions in the payment industry. Payment card industry compliance refers to the technical and operational standards that businesses follow to secure and protect credit card data provided by cardholders and transmitted through card processing transactions.
PCI compliance is critical because customers expect companies to protect payment profileholder data. Data breaches face legal and business penalties, and companies that don't take security seriously are sure to damage the trust of customers and organizations that meet PCI requirements. PCI compliance also requires attention to detail. By following each recommendation in the checklist, organizations can protect their technical and operational systems. And they will also be immune from fines caused by non-compliance.

- install and maintain a firewall, Firewalls are the first line of defense against external threats. PCI-compliant organizations must implement firewalls at the edge of the network. The network firewall configuration should block unauthenticated traffic and limit public access to the Cardholder Data Environment (CDE). All devices connected to the network must be protected by a firewall, without exception.
- reconfigure vendor default settings, Devices and apps from third-party vendors usually come with default settings. Hackers often use default passwords that are publicly available and widely known. If hackers compromise a single asset through default passwords, they may gain access to a wider network. Compliant payment providers must change all default passwords before deploying assets. System components must have custom settings that comply with network security standards. Access to assets must be protected with encryption and strong passwords. This also applies to any shared infrastructure or application. Partners must change the default passwords on the server administration side. Compliant payment providers should double-check that this has been done.
- protect stored cardholder data, Protecting the CDE is the most important task of PCI-DSS compliance. Payment providers need to know where cardholder information flows. They must capture and secure all databases that store cardholder information. And all credit card information must be protected with strong encryption. Databases containing cardholder data must be separate from other network resources. To ensure data security, each part must be thoroughly checked and monitored. Data retention is another key compliance requirement. Data must be securely deleted. Payment providers must hide Payment Account Numbers (PANs) that cannot be encrypted. Encryption keys also need to be protected. PCI rules require that keys be encrypted and stored securely.
- encrypt transmitted cardholder data, Protecting static data is not enough. To meet PCI-DSS compliance requirements, organizations must also transmit cardholder data securely. Payment providers should apply strong encryption to all data transfers. They must use approved protocols, such as later versions of TLS. It is important to check that your protocols comply with the most recent PCI-DSS regulations. And PANs should never be transmitted in plain text format.
- protect against malware, Malware is a major attack factor for data breaches. PCI-DSS-compliant payment providers must take steps to detect, neutralize, and destroy malware before it can cause damage or steal data. Payment providers must update all antivirus software to the latest version. And threat detection tools should generate reports for use in PCI-DSS audits. In addition, they should protect the CDE with the help of threat detection tools. And they should educate network users to reduce phishing risks. This includes increasing awareness of malicious attachments and the use of external devices.
- create and apply a cybersecurity policy, The core aim of this section is to show that payment providers have identified core threats and put in place measures to handle them. This
requires continuous security assessment and auditing.
- Identifying potential attack vectors
- Categorizing the risk level of each asset
- Documenting security controls to mitigate risks
- maintain the security of critical systems and applications, Access control systems should protect the CDE against unauthorized intruders. Payment providers should implement a zero-trust model that limits access on a need-to-know basis. Payment providers should put strong authentication systems in place to restrict access to legitimate users. PCI recommends the use of multi-factor authentication (MFA) or two-factor authentication (2FA) systems. Both systems require more than one authentication factor. This makes it much harder for outsiders to gain access.
- continuously test security systems, Based on PCI regulations, a unique ID should be created for each network user. User activity should be logged and easily tracked. Systems must log every access request and session metadata. And this information should be available during the audit. PCI-DSS regulations also require tight control over shared accounts. Payment providers should minimize the number of group accounts and document why such accounts are required. Users should be educated about the risks of sharing credentials with others. And security teams should routinely audit access policies to prohibit unsafe access.
- track and monitor network access, Access controls must be applied to all devices involved in the CDE. If a device receives, transmits, or stores cardholder information, it must be accessible only to authorized users. This applies to devices that can connect to CDE, even if they do not use credit card data. It also covers paper assets that store cardholder data. Payment providers must establish physical access controls, such as card readers or locks. And they should also monitor the physical environment through security cameras. Cameras should capture all access points and critical assets. PCI-DSS rules require that access records be stored for at least 90 days. Records should show who entered sensitive areas, and there should be individual records for foreign visitors. Physical access controls also apply to mobile devices and storage peripherals containing cardholder data. These devices must always be secure. And they must be destroyed after use to eliminate the risk of information theft.
- restrict physical access to data cardholder data, Vulnerabilities in physical and wireless networks make it easier for cybercriminals to steal information. This requirement requires that all systems have the correct auditing policy and send logs to a centralized syslog server. These reports should be reviewed at least daily to look for anomalies and suspicious activity. Security information and event monitoring (SIEM) tools can help you log system and network activity, monitor logs, and alert you to suspicious activity. PCI DSS also requires that audit trail records meet a certain standard in terms of the information contained. Time synchronization is required. Audit data must be secure, and such data must be retained for at least one year.
- identify and authorize all users, PCI compliance requires regular network testing at all levels. External and internal network tests should be carried out by an approved scanning vendor (ASV). Network tests should scan for vulnerabilities, such as insecure endpoints. Tests should document any weaknesses. Security teams should record subsequent actions taken to secure network assets. Annual penetration testing is required at higher PCI levels and is advisable for all compliant payment providers. Penetration tests should always follow major system-level changes. They should simulate the main data breach risks.
- restrict access to cardholder data, Documentation is a critical aspect of PCI compliance. All payment providers must create and implement a network-wide information security policy. This policy includes all of the security controls present on the network and documents how each control relates to PCI compliance. The information security policy explains how users can safely access sensitive data. It includes details about the payment provider's incident response plan, including threat mitigation and system recovery. And it also explains third-party requirements. Policies should be subject to an annual review. Security teams should review whether current systems are capable of countering critical risks. And annual updates should bring policies into line with PCI best practices.
osstmm
The Open Source Security Testing Methodology Manual, or OSSTMM is a methodology to test the operational security of physical locations, workflow, human security testing, physical security testing, wireless security testing, telecommunication security testing, data network security testing, and compliance.
OSSTMM can be a supporting reference for ISO 27001 instead of a hands-on or technical application penetration testing guide. OSSTMM includes the following key sections:
- security analysis
- operational security metrics
- trust analysis
- workflow
- human security testing
- physical security testing
- wireless security testing
- telecommunications security testing
- data network security testing
- compliance regulations
- reporting with the STAR (Security Test Audit Report)
payment gateway
The Nette ecosystem introduces a robust and adaptable payment gateway infrastructure powered by Paynette, offering seamless and secure payment processing across a variety of platforms. Whether facilitating everyday transactions, managing virtual pools, or enabling token-based payments, Paynette serves as the backbone of the ecosystem's financial operations.
A payment gateway is the central mechanism that collects, transmits, and authorizes payment data in real-time, ensuring smooth interactions between users and merchants. In the Nette ecosystem, this functionality is enhanced by blockchain technology, providing multi-chain support and unparalleled security.
Key Features of Paynette's Payment Gateway
- Multi-Chain Support
- Paynette integrates blockchain technology to provide a seamless, decentralized framework for transactions, enabling cross-platform and multi-chain capabilities.
- Global Accessibility
- Designed to cater to businesses and users worldwide, Paynette facilitates frictionless cross-border transactions, empowering users to transact confidently in the Nette ecosystem.
- Enhanced Security
- Every transaction is safeguarded with blockchain encryption, ensuring transparency, immutability, and protection against fraud.
- Scalable Design
- Whether for high-frequency trading in Tradenette or ICO campaigns for Coinette, Paynette scales effortlessly to meet diverse transaction demands.
- Token Integration
- Fully optimized for Coinette (QUI) transactions, making it the go-to solution for token-based payments and investments in the Nette ecosystem.
Why Paynette Stands Out in the Nette Ecosystem
The Paynette payment gateway combines traditional payment solutions with the transformative power of blockchain. Its infrastructure is designed to:
- Empower businesses of all sizes, from startups to global enterprises.
- Foster trust and efficiency in virtual asset transactions.
- Adapt to future financial technologies, ensuring longevity and innovation.
By integrating advanced payment gateway capabilities, the Nette ecosystem redefines the standards of secure, scalable, and user-centric financial solutions.
infrastracture
The Nette ecosystem leverages advanced payment gateway technology to streamline financial transactions across its platforms, such as Paynette. A payment gateway serves as the central component of the payment processing system, facilitating the secure collection, transmission, and authorization of customer information in real time. Here's how payment gateways function within the Nette ecosystem and the types available:
Types of Payment Gateways in the Nette Ecosystem
- On-Site Payments
- How It Works: Large-scale enterprises can use on-site payment systems where both the checkout and payment processing occur on their own servers, fully integrated with the Paynette system.
- Advantages in Nette Ecosystem:
- Offers full control over the user experience.
- Enhanced security through blockchain-based multi-chain transactions.
- Ideal for businesses requiring custom payment solutions.
- Checkout On-Site, Payment Off-Site
- It Works: The front-end checkout happens on the merchant's website, but the payment is processed securely via the back-end of the payment gateway.
- Advantages in Nette Ecosystem:
- Simplifies integration with external payment processors while ensuring robust security.
- Suitable for mid-sized businesses seeking secure yet straightforward payment solutions.
- Redirects
- How It Works: Customers are redirected to an external payment gateway, such as Paynette, to complete their transaction.
- Advantages in Nette Ecosystem:
- Ideal for small businesses that benefit from the simplicity and security of larger platforms.
- Reduces operational complexity for merchants while ensuring compliance and security.
Why the Nette Ecosystem Stands Out
The Paynette platform, a core part of the Nette ecosystem, enhances payment gateway functionality by:
- Blockchain Integration: Multi-chain technology ensures secure, fast, and cost-efficient transactions.
- Global Reach: Paynette enables seamless cross-border payments for businesses and consumers.
- Modular Flexibility: Adapts to the needs of different business scales, from startups to enterprises.
By combining traditional payment gateway methods with blockchain innovation, the Nette ecosystem delivers a robust and versatile infrastructure for businesses in diverse markets.
traditional banking
Traditional banking has existed for centuries and is distinguished by its physical branches, regional headquarters, branded ATMs, extensive staffing, and personalized customer service through dedicated account managers. Although traditional banks now offer online services, their primary focus remains on maintaining a strong physical presence.
One key reason many customers prefer traditional banking is the direct, face-to-face service it provides. A global consumer banking survey highlights that live interactions foster trust and credibility, making personal connections a critical advantage for traditional banks.
Customers often choose to visit physical branches for financial advice or when purchasing new products. The ability to interact with a real person provides reassurance, especially for significant tasks like opening a bank account.
Despite their reliance on physical locations, traditional banks have increasingly embraced digital solutions. Recognizing the evolving needs and preferences of their clients, many have introduced online banking services, mobile applications, and robust digital platforms, bridging the gap between traditional and online banking experiences.
neobanking
Neobanking in the Nette Ecosystem The term "neo" signifies newness, and neobanks represent a modern approach to banking, operating entirely online without any physical branches. These digital-first banks provide a wide range of financial services, including payments, money transfers, lending, deposits, withdrawals, debit cards, and investment options. However, most neobanks lack banking licenses and rely on partnerships with licensed traditional banks to deliver their services. Neobanks are not merely digital alternatives to traditional banking but pioneers in transforming the financial landscape. For instance, Chime, a leading neobank, ranked among the top 10 banks in the United States in 2021, growing from 13 million customers to over 21 million users today. This meteoric rise illustrates the disruptive potential of neobanks.
Key Differentiators
While traditional banks offer a comprehensive suite of services such as checking accounts, savings accounts, loans, credit cards, and investments, neobanks stand out by focusing on user-friendly, low-cost financial solutions. Key benefits include:
- Minimal Fees: Neobanks often offer no-fee services, including overdraft protection and low-cost transactions.
- Digital-First Tools: Advanced tools to support financial health and transparency.
- Efficiency: Lower operational costs due to the absence of physical branches.
Revenue Models
Neobanks sustain their operations through innovative and streamlined revenue models:
- Transaction Fees: While most accounts are fee-free, small fees are charged for services like wire transfers or ATM withdrawals.
- Subscription Fees: Premium services for personal or business accounts are offered for a monthly subscription fee.
- Loan Interest: Some neobanks provide credit cards and loans, generating income through interest rates.
Each neobank employs unique strategies, resulting in varied fee structures and service offerings. Their reduced overhead enables neobanks to achieve profitability with lower revenue requirements compared to traditional banks.
Neobanks in the Nette Ecosystem
In the Nette ecosystem, neobanking aligns seamlessly with the platform's modular, multi-chain, and decentralized architecture. Neobanks can leverage the ecosystem's blockchain-based infrastructure to:
- Enhance transparency and security in financial transactions.
- Facilitate cross-border payments using the Coinette™ token.
- Offer decentralized financial services integrated with other Nette ecosystem platforms, such as Paynette for modular payments and Tradenette for investment and trading solutions.
Neobanks, powered by the Nette ecosystem, represent the future of banking, combining the agility of digital services with the robustness of blockchain innovation.
| Aspect | Traditional Banking | Neobank | Nette Ecosystem Advantage |
|---|---|---|---|
| Physical Presence | Operates through physical branches, self-branded ATMs, and regional headquarters. | Fully digital, no physical branches. | Blockchain-powered services eliminate the need for physical infrastructure, reducing costs. |
| Customer Interaction | Offers face-to-face interactions with dedicated account managers and in-branch consultations. | Relies on AI-driven chatbots, apps, and online support for customer service. | Combines smart contract-based automation with user-friendly platforms like Paynette. |
| Fees | Typically charges higher fees for account maintenance, overdrafts, and transactions. | Low to no fees, focusing on transparent pricing and cost-efficiency. | Uses Coinette™ for low-cost, multi-chain transactions across the ecosystem. |
| Speed of Services | Slower due to manual processing and reliance on legacy systems. | Instantaneous digital processes and quick approvals. | Real-time blockchain settlements ensure speed and accuracy. |
| Accessibility | Limited to working hours and physical branch availability. | Available 24/7 with access through mobile apps and web portals. | Enables uninterrupted financial operations globally through decentralized services. |
| Revenue Model | Profits from interest, fees, and complex investment mechanisms. | Generates revenue from transaction fees, subscription services, and loans. | Smart contract automation reduces operational costs, creating efficient revenue streams. |
| Security | Relies on centralized systems, making them prone to breaches and fraud. | Focuses on secure digital encryption but faces risks from centralized data repositories. | Employs decentralized blockchain, ensuring high-level data integrity and security. |
| Product Offering | Comprehensive suite: deposits, loans, credit cards, investments, and insurance. | Focused on payments, transfers, lending, and budgeting tools with fewer product varieties. | Modular platforms like Tradenette and Paynette allow tailored, scalable solutions. |
| Global Reach | Complicated and slow international transactions. | Facilitates cross-border payments but depends on partnerships with licensed banks. | Multi-chain compatibility ensures seamless global transactions using Coinette™. |
| Adaptability | Slow to adapt to technological advancements due to legacy systems and regulations. | Highly adaptive, introducing new features and technologies quickly. | Nette ecosystem's decentralized framework fosters rapid innovation and adaptability. |
| User Experience | Traditional, with emphasis on in-branch engagement and manual processes. | Intuitive, app-based experience with AI and digital tools. | Unified interfaces in Nette ecosystem apps enhance the user journey across platforms. |
blockchain as a Service
Blockchain-as-a-Service (BaaS) enables businesses to build and manage blockchain-based applications using cloud-based infrastructure provided by third-party service providers. This model simplifies blockchain adoption by removing the complexities and operational costs of creating, configuring, and maintaining blockchain infrastructure, allowing businesses to focus on their core objectives.
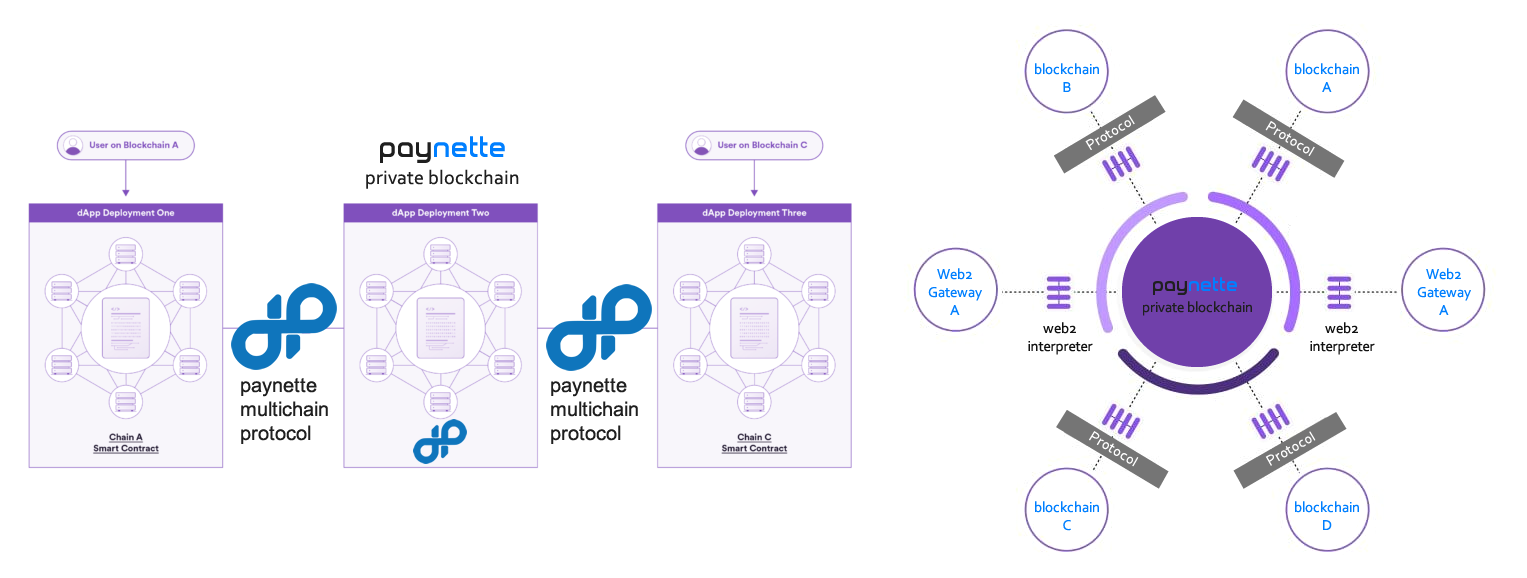
In the Nette Ecosystem, Paynette™ provides an advanced BaaS solution tailored for financial applications. Leveraging the ecosystem's secure and scalable infrastructure, Paynette empowers developers to build, deploy, and manage blockchain applications with ease. Its services include:
- Hosting: Developers can quickly deploy blockchain networks using the Paynette platform within the AWS cloud environment. Support for additional cloud providers like Azure and Alibaba Cloud will be available by late 2024.
- Private Blockchain Network: Paynette facilitates the setup of secure private blockchain networks. These networks allow selective transaction verification across other private networks, ensuring both privacy and interoperability.
- Administrator Toolkit: Paynette offers a suite of management tools to streamline the automation, deployment, and monitoring of blockchain networks and applications.
- Integration: Paynette provides industry-standard solutions for seamless integration of blockchain applications into existing enterprise systems, accelerating adoption across businesses.
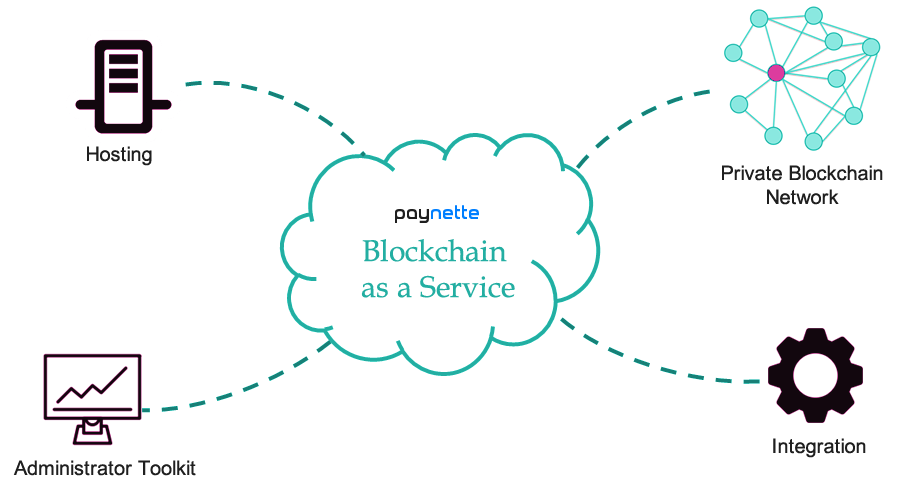
Paynette's BaaS aligns with the Nette Ecosystem's commitment to delivering scalable, efficient, and user-friendly blockchain solutions. It lowers barriers to blockchain adoption, enabling developers and enterprises to innovate in financial technology and beyond.
multi-chain
The Nette Ecosystem incorporates a multi-chain architecture to enhance scalability, interoperability, and efficiency across its services, including Paynette™, Tradenette™, and Coinette™. A multi-chain system allows the coexistence and interaction of multiple blockchain networks within a unified ecosystem, each optimized for specific use cases. By distributing workloads across various chains, the Nette Ecosystem avoids congestion, reduces transaction fees, and accelerates processing times, making it a robust solution for modern decentralized applications (dApps) and financial platforms.
Features of Multi-Chain in the Nette Ecosystem:
- Dedicated Chains for Specialized Functions: Each blockchain in the multi-chain system is tailored to handle specific services, such as payment processing, trading, or token management. This specialization ensures high performance and reliability for each function.
- Enhanced Scalability: By distributing transactions across multiple chains, the Nette Ecosystem minimizes bottlenecks and achieves a higher throughput, enabling seamless operation even during peak usage.
- Interoperability within the Ecosystem: The multi-chain structure allows seamless communication and data exchange between the chains. Paynette™ utilizes this capability to provide instant financial services, while Tradenette™ leverages it for real-time market analysis and trading operations.
- Security and Redundancy: Independent blockchains within the system reduce the risk of a single point of failure. Each chain is fortified with the Nette Ecosystem's proprietary security protocols to ensure data integrity and user trust.
- Efficient Resource Allocation: Multi-chain architecture allows dynamic allocation of computational resources based on demand, ensuring optimal network performance for users and developers alike.
Difference Between Multi-Chain and Cross-Chain
While both multi-chain and cross-chain approaches aim to enhance blockchain functionality and connectivity, they differ fundamentally in their design and objectives:
| Aspect | Multi-Chain | Cross-Chain |
|---|---|---|
| Definition | Multiple independent blockchains operating within a single ecosystem for specific tasks. | A mechanism that connects separate and unrelated blockchains to enable data and asset transfer. |
| Objective | To optimize performance by distributing tasks across specialized blockchains. | To facilitate interoperability and communication between entirely different blockchain networks. |
| Interaction | Focused on internal communication within the ecosystem's chains. | Enables external communication between independent blockchain ecosystems. |
| Example in Nette | Paynette's multi-chain infrastructure for handling payments, trading, and token management. | Future dPAP-based solutions for bridging assets between Nette Ecosystem and external blockchains. |
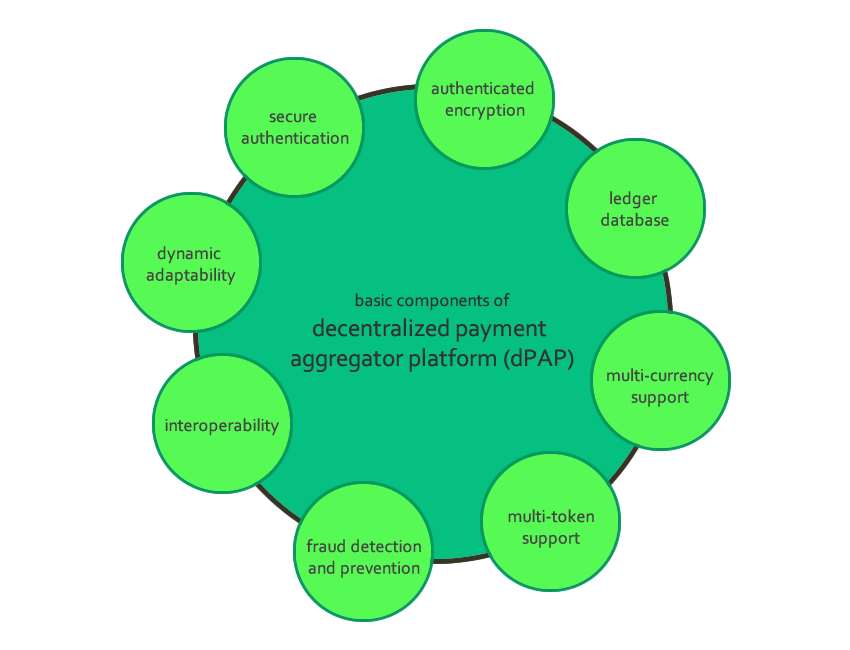
basic components
Setting priorities is important when architecting a dPAP. A balance must be struck between business goals, customer needs, updateability, and security. We know it is not easy. It may seem like a good idea to make the dPAP as versatile as possible. But if we start by focusing on the most basic features, you'll get more done.
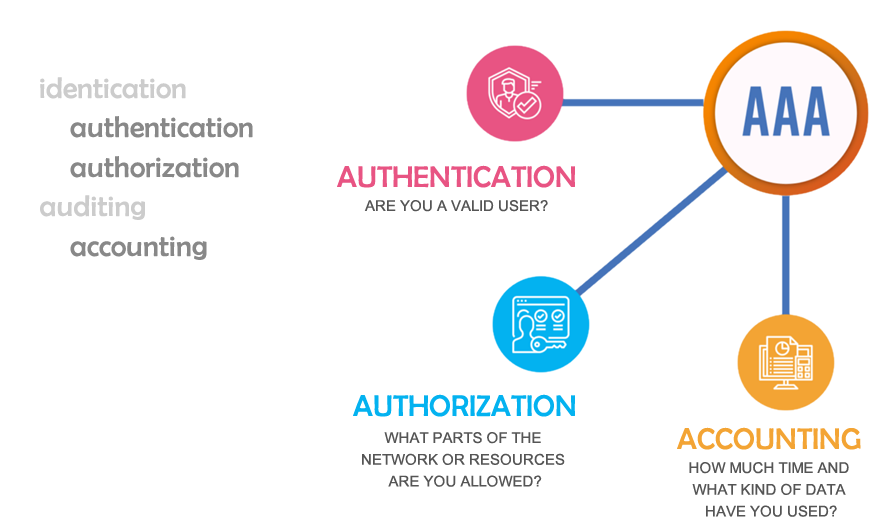
authentication, authorization, & accounting
The Nette ecosystem places Authentication, Authorization, and Accounting (AAA) at the heart of its architecture, ensuring robust, secure, and scalable management of user access and activities. AAA is critical for fostering trust and transparency across the ecosystem's services, including Tradenette, Paynette, and Coinette token operations.
1. authentication: verifying user identity
Authentication is the first step in securing the Nette ecosystem. It confirms the identity of users before granting them access to services and resources.
Key Features in Nette
- Multi-Factor Authentication (MFA):
- Combines password-based login with additional verification steps, such as email or SMS OTPs, to enhance security.
- Ensures that critical services like Paynette and Tradenette remain protected against unauthorized access.
- Blockchain-Integrated Identity Management:
- Users are verified through blockchain-based identity tokens, reducing the risk of identity theft.
- Simplifies authentication for services across the ecosystem, creating a seamless experience.
- KYC Integration:
- Tradenette users undergo a robust Know Your Customer (KYC) process, including document verification and biometric checks, ensuring regulatory compliance.
- Custom workflows adapt based on the user's role, such as investor or pool owner.
Authentication in Action
- A Tradenette user logs in to access trading pools:
- Credentials are validated using blockchain-backed ID tokens.
- Sensitive actions, like withdrawals, trigger MFA for additional security.
2. Authorization: Controlling Access and Permissions
Authorization determines what users can access or perform after authentication. It ensures that users interact with the system according to their roles and privileges.
Key Features in Nette
- Role-Based Access Control (RBAC):
- Users are assigned roles, such as pool manager, trader, or public user, each with specific permissions.
- Tradenette, for example, restricts sensitive financial settings to pool managers while enabling traders to perform market activities.
- Tokenized Access Management:
- Leveraging Coinette (QUI) tokens, users can gain temporary or tiered access to specific services based on their token holdings.
- Example: Higher Coinette holdings unlock advanced trading analytics or premium support.
- Dynamic API Authorization:
- External services and third-party integrations are given API access tokens with fine-grained permissions.
- Revocation and refresh mechanisms ensure security during ongoing integrations.
Authorization in Action
- A virtual pool manager accesses financial reports:
- RBAC ensures only authorized managers can view or edit sensitive data.
- APIs securely pull real-time data without exposing the entire system to vulnerabilities.
3. Accounting: Ensuring Transparency and Accountability
Accounting logs every interaction and transaction, creating an immutable audit trail for user activities within the ecosystem. This enables trust, regulatory compliance, and operational insights.
Key Features in Nette
- Activity Logging:
- Every action be it a trade on Tradenette, a payment on Paynette, or a token transfer—is recorded in real-time.
- Logs are enriched with metadata, such as user ID, timestamp, and location.
- Immutable Blockchain Records:
- Accounting data is anchored on the blockchain, ensuring records cannot be tampered with.
- Useful for audits and dispute resolution.
- Customizable Reporting Tools:
- Virtual pool managers can generate transaction and user activity reports on Tradenette.
- Paynette offers revenue breakdowns for businesses leveraging its payment gateway.
- Automated Alerts:
- Irregular activities, such as unusually high withdrawals or multiple failed login attempts, trigger automated alerts for administrators.
Accounting in Action
- A trader disputes a failed transaction:
- Accounting records provide an auditable log of the transaction's lifecycle.
- Immutable blockchain records resolve disputes quickly by offering verifiable data.
Integration Across the Nette Ecosystem
- Tradenette
- Authentication: Enables secure login for traders and investors using blockchain-backed credentials.
- Authorization: Limits user actions based on roles; for instance, investors can only fund pools, not manage them.
- Accounting: Tracks trades, deposits, and pool activities with detailed reporting tools.
- Paynette
- Authentication: Secure access for merchants and customers using MFA and encrypted data exchanges.
- Authorization: Merchants can manage payment settings while customers can initiate or track transactions.
- Accounting: Logs every payment and refund for transparent financial reporting.
- Coinette
- Authentication: Blockchain-based identity tokens ensure seamless token management.
- Authorization: Enables tiered benefits for users based on token holdings.
- Accounting Tracks token minting, transfers, and staking activities for complete transparency.
Why AAA Matters in the Nette Ecosystem
- Enhanced Security:
- Protects user data and financial assets from unauthorized access.
- Regulatory Compliance:
- Simplifies adherence to global standards for financial platforms.
- Operational Transparency:
- Builds trust with users and stakeholders through immutable records.
- Scalability:
- AAA mechanisms are designed to support the ecosystem's growth without performance trade-offs.
By embedding AAA into its core infrastructure, the Nette ecosystem ensures its services remain secure, user-friendly, and future-proof, fostering trust and confidence in a rapidly evolving digital landscape.
authenticated encryption
Encryption is a foundational pillar of the Nette ecosystem, ensuring data privacy, authenticity, and integrity across its interconnected services like Tradenette and Paynette. By leveraging advanced encryption techniques, the Nette ecosystem safeguards sensitive information, facilitates secure transactions, and maintains user trust.
1. Privacy and Confidentiality
The primary goal of encryption is to protect the confidentiality of data. In the Nette ecosystem, this is achieved through robust encryption algorithms that ensure sensitive information remains accessible only to authorized parties.
- Encryption and Decryption Process:
Data is encrypted using secure algorithms, and decryption requires the appropriate key, ensuring that unauthorized access is virtually impossible. - Applications:
- Protecting user credentials during authentication.
- Securing financial transactions and token transfers within the ecosystem.
2. Data Integrity and Authenticity
Beyond confidentiality, ensuring data integrity is critical in preventing unauthorized alterations to information. The Nette ecosystem employs digital signatures and Message Authentication Codes (MAC) to verify the authenticity and integrity of data.
Message Authentication Code (MAC)
MAC is used to ensure that transmitted data has not been tampered with. A symmetric key shared between the sender and receiver generates an authentication tag, allowing verification of data integrity.
- Properties of MAC:
- Authenticity: Only those with the secret key can create a valid MAC tag.
- Symmetry: The same key is used for both generating and verifying the tag.
- Applications in Nette:
- Verifying transaction integrity on Paynette.
- Authenticating inter-service communication between Tradenette and Coinette.
Digital Signatures
Digital signatures provide non-repudiable proof of origin and authenticity, ensuring that any tampering or unauthorized changes to data are easily detectable.
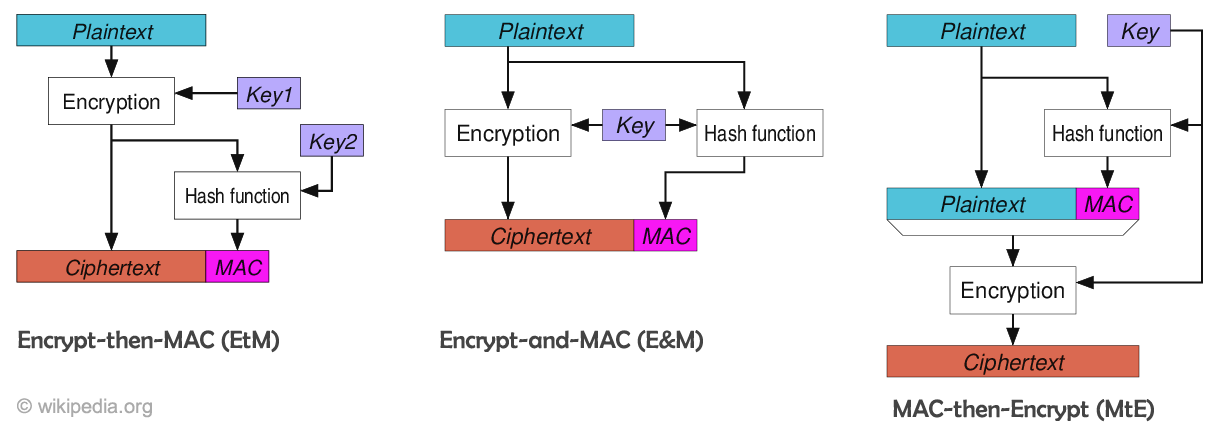
2. Data Integrity and Authenticity
The Nette ecosystem relies on Authenticated Encryption with Associated Data (AEAD) as the primary encryption primitive for securing sensitive communications and operations. AEAD combines encryption and authentication in a single process, making it both secure and efficient.
Key Properties of AEAD:
- Secrecy: Prevents exposure of plaintext, except for its length.
- Authenticity: Detects unauthorized changes to the ciphertext or the underlying plaintext.
- Symmetry: Uses the same key for encryption and decryption.
- Randomization: Encryption is randomized to produce unique ciphertexts for identical plaintexts.
To handle cases where deterministic behavior is required, Deterministic AEAD is used to ensure identical ciphertexts for the same plaintext input while preserving security.
Applications in Nette:
- Encrypting user data during transactions on Tradenette.
- Securing API communications between Paynette and third-party integrations.
Advanced Techniques in Nette
HMAC (Hash-based Message Authentication Code)
To enhance performance, the Nette ecosystem uses HMAC, which combines hashing with a secret key. This ensures efficient and secure computation of authentication tags.
- Speed: Operates at the speed of the underlying hash algorithm (e.g., SHA-256).
- Security: Resistant to cryptographic attacks due to its robust design.
CBC-MAC (Cipher Block Chaining MAC)
For environments requiring block cipher-based authentication, CBC-MAC is employed. By encrypting data in blocks and producing a truncated tag, CBC-MAC ensures secure authentication, particularly when using modern algorithms like AES.
Why Encryption is Critical in Nette
The Nette ecosystem's encryption framework aligns with its mission to provide a secure, user-centric environment. Key benefits include:
- End-to-End Security: Protects data throughout its lifecycle, from input to processing and storage.
- Regulatory Compliance: Meets global security standards for financial and trading platforms.
- User Trust: Builds confidence in the ecosystem's ability to safeguard personal and financial data.
By integrating encryption techniques like MAC, HMAC, and AEAD, the Nette ecosystem ensures that its services remain resilient, secure, and scalable in an ever-evolving digital landscape.
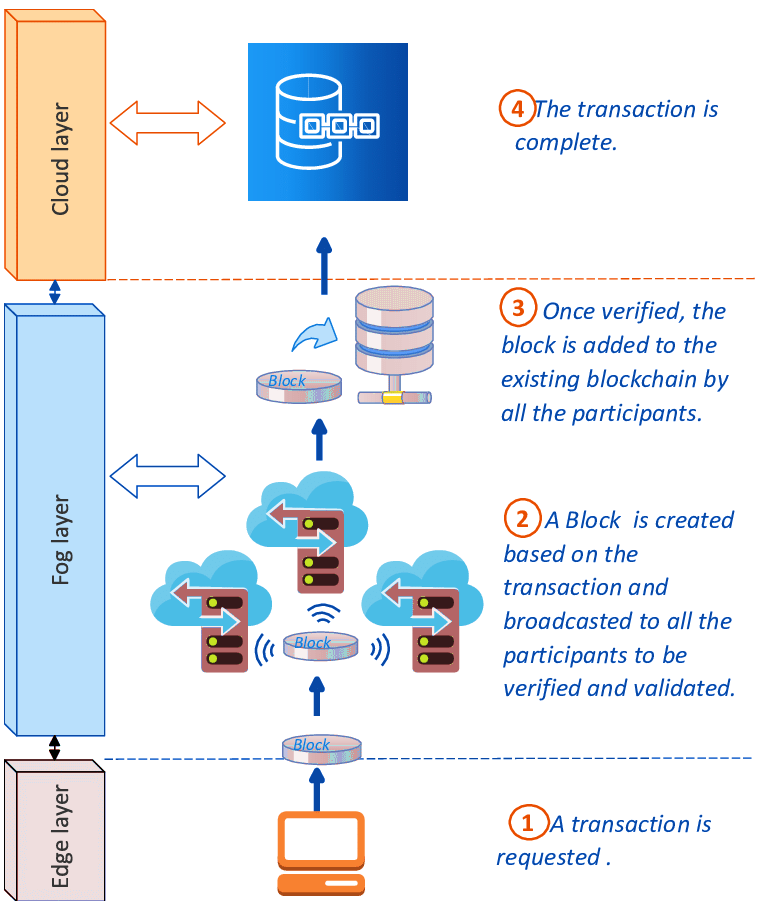
ledger database
In the Nette ecosystem, a ledger database serves as a secure and immutable repository for recording financial and transactional data. This concept builds upon the age-old principle of ledgers but incorporates modern cryptographic techniques, including blockchain, to ensure data integrity, transparency, and tamper resistance.
Immutable Transactions
A ledger database records transactions cryptographically, making them:
- Permanent: Transactions are permanently stored and cannot be altered.
- Tamper-Proof: The cryptographic techniques ensure immutability, safeguarding data against unauthorized changes.
- Transparent: Immutability enhances data integrity and boosts user confidence in the system.
In blockchain-based ledger databases, immutability is achieved through distributed ledger technology (DLT), where data is stored and accessed across decentralized nodes. While distributed blockchain is a common implementation, it is not the sole option; private and permissioned blockchain methods can also be leveraged.
The Nette ecosystem's database ledger integrates cutting-edge cryptographic and database technologies to provide secure, scalable, and transparent management of financial and transactional data. At its core, the ledger facilitates immutability, accountability, and decentralization, making it a cornerstone for services like Tradenette, Paynette, and other Nette platforms.
Key Features of the Nette Ledger Database
- Immutability:
- Transactions are permanently recorded using cryptographic hashes.
- Every transaction is time-stamped, ensuring a reliable history that cannot be altered or deleted.
- Tamper-proof mechanisms ensure data integrity, fostering trust among users.
- Transparency:
- Transactions are visible to authorized parties, enabling accountability without compromising security.
- Public or permissioned access ensures that the right stakeholders have access to the data.
- Security:
- Uses elliptic curve cryptography (ECC) for signing and validating transactions.
- Supports encryption for data at rest and in transit, protecting sensitive information.
- Built-in mechanisms for fraud detection and anomaly tracking.
- Decentralization and Distribution:
- Designed to operate as a distributed ledger across multiple nodes, enhancing resilience.
- Can operate as a hybrid model, balancing decentralization with controlled oversight.
- Scalability
- Capable of handling high transaction throughput, essential for platforms like Tradenette and Paynette.
- Utilizes sharding and parallel processing to improve performance under heavy loads.
- Integration with NoSQL:
- The ecosystem leverages, a multi-model NoSQL database, for storing and querying complex data relationships.
- NoSQL's native graph capabilities make it ideal for tracking interconnected ledger entries and relationships across accounts, tokens, and transactions.
Mechanisms of the Nette Ledger Database
- Transaction Verification:
- Transactions are validated using cryptographic hashes to ensure authenticity.
- For private ledgers, a consensus authority (or validator nodes) ensures rapid transaction approval.
- For public systems, consensus is achieved using algorithms like Proof of Stake (PoS) or Delegated Proof of Stake (DPoS).
- Block Creation:
- Transactions are grouped into blocks.
- Each block contains:
- A cryptographic hash of the previous block.
- A list of validated transactions.
- A timestamp and metadata for auditing purposes.
- Chaining and Immutability:
- Each block references the hash of its predecessor, forming a blockchain.
- Modifying any block would invalidate the entire chain, ensuring data cannot be tampered with retroactively.
- Permissioned Access (Hybrid Models):
- Supports role-based access control (RBAC) for permissioned environments.
- Allows enterprises and specific stakeholders to manage sensitive operations securely.
- Combines private and public blockchain features to balance transparency and control.
- Smart Contracts and Automation:
- Implements smart contracts for automated execution of predefined rules, e.g., token transfers, escrow services, or compliance verification.
- Ensures that operational workflows across platforms like Tradenette and Paynette are reliable and efficient.
- Interoperability with Nette Services:
- Seamless integration with Tradenette's trading platform for asset tracking and pool management.
- Real-time synchronization with Paynette for token-based payment processing.
- Enables token issuance and tracking for the Coinette (QUI) token, ensuring compliance and transparency.
Database Types and Models in the Nette Ledger
- Distributed Ledger:
- Each node contains a synchronized copy of the ledger.
- Ideal for decentralized applications like asset trading or public token issuance.
- Permissioned Ledger:
- Centralized control with selective decentralization for better performance.
- Used for sensitive operations such as investor profiling and KYC data in Tradenette.
- Hybrid Ledger Models:
- Combines private control for sensitive operations with public visibility for certain aspects, ensuring compliance without sacrificing transparency.
- Graph-based Ledger Tracking:
- NoSQL's graph capabilities enable complex queries across:
- Token transfers.
- Investor relationships.
- Asset pools and virtual fund ownerships.
- NoSQL's graph capabilities enable complex queries across:
Advanced Capabilities
- Consensus Algorithms:
- Implements DPoS for efficient transaction validation in the public blockchain model.
- Private implementations use faster consensus mechanisms like Raft or PBFT (Practical Byzantine Fault Tolerance) for low-latency operations.
- Token Management:
- The ledger natively supports the issuance, transfer, and burning of tokens like Coinette (QUI).
- Tracks ownership and movement of tokens to prevent double-spending and ensure transparency.
- Auditing and Compliance:
- Built-in tools for tracking and auditing transactions.
- Compliance with financial regulations (e.g., AML/KYC) is ensured through robust logging and traceability.
- Real-time Analytics:
- Integrated analytics tools provide insights into transaction trends, user activity, and token flow.
- Supports predictive models for fraud detection and market analysis.
Future of the Nette Ledger
The Nette ecosystem's ledger database continues to evolve, incorporating:
- Cross-chain compatibility to integrate with other blockchains for broader asset interoperability.
- Quantum-resilient cryptography to future-proof against emerging threats.
- Green consensus mechanisms to reduce energy consumption and align with sustainability goals.
This robust ledger architecture positions the Nette ecosystem as a leader in secure, transparent, and scalable financial systems tailored for modern decentralized and hybrid applications.
assets
Overview of Crypto Assets Crypto assets are digital representations of value that leverage cryptography, peer-to-peer networks, and public ledgers to ensure secure, decentralized operations. Unlike traditional assets, they eliminate intermediaries, reducing costs and increasing efficiency in various industries, from payments and file sharing to IoT applications.
Crypto assets operate independently of central authorities like banks or governments. However, they are subject to tax rules similar to other assets, based on how they are acquired, held, or disposed of. While most crypto assets are not classified as securities, certain contractual arrangements through centralized trading platforms (CTPs) may invoke securities regulations.
Types of Crypto Assets
The Nette ecosystem categorizes crypto assets into the following types:
- Payment Currencies
Designed for payments, these assets leverage blockchain technology to securely transfer funds. Examples include Bitcoin (BTC) and Litecoin (LTC), which are widely accepted for goods and services. - Blockchain Economies (Mainnets)
Platforms that extend blockchain functionality beyond payments. Ethereum (ETH), Tron (TRX), and Solana (SOL) allow decentralized applications (dApps) and token creation. - Privacy Coins
Offer enhanced privacy by anonymizing transaction details. Examples: Monero (XMR) and Dash (DASH). - Stablecoins
Pegged to stable assets like fiat currencies to minimize volatility. Examples: Tether (USDT), USD Coin (USDC), and DAI. - Utility Tokens
Power specific blockchain-based platforms or services. Most are built on Ethereum (ERC-20) or Tron (TRC-20) networks. Example: Coinette (QUI), the native utility token of the Nette ecosystem. - Security Tokens
Represent ownership or stake in a project, offering returns similar to securities. Example: KuCoin Shares (KCS). - Non-Fungible Tokens (NFTs)
Unique digital assets with value derived from rarity, used for collectibles, digital art, and more. Example: Cryptokitties (ERC-721). - Decentralized Finance (DeFi) Tokens
Power decentralized financial services, including lending, staking, and exchanges. Examples: Chainlink (LINK) and Compound (COMP).
The Howey Test and Regulatory Framework
The Howey Test determines whether an asset qualifies as a security by evaluating:
- Monetary investment.
- In a common enterprise.
- With an expectation of profit.
- Derived from the efforts of others.
Assets meeting these criteria are regulated as securities. The Nette ecosystem ensures compliance with these regulations, especially for security tokens and services provided via CTPs.
Supported Currencies and Tokens in the Nette Ecosystem
The ecosystem currently supports the following assets, with plans to expand:
- Fiat Currencies
- United Arab Emirates Dirham (AED)
- United States Dollar (USD) (under review)
- Euro (EUR) (under review)
- Utility Tokens
- Coinette (QUI): Nette's native utility token.
- Stablecoins
- Tether (USDT)
- USD Coin (USDC)
- Binance USD (BUSD)
- DAI (DAI)
- Other prominent stablecoins like Pax Dollar (USDP) and Liquity USD (LUSD).
- Security Tokens
- KuCoin Shares (KCS).
- Mainnets
- Bitcoin (BTC)
- Ethereum (ETH)
- Tron (TRX)
- Algorand (ALGO)
- Avalanche (AVAX)
- Solana (SOL)
Other assets and tokens will be announced as the ecosystem evolves.
Advantages of Crypto Assets in the Nette Ecosystem
- Decentralization: Reduction of middlemen and associated costs.
- Flexibility: Wide applications across industries.
- Transparency: Enhanced by public ledger technology.
- Interoperability: Compatibility with diverse blockchains and token standards.
The Nette ecosystem leverages these strengths to facilitate secure, scalable, and user-centric financial operations while remaining adaptable to evolving market needs.
decentralized cloud computing
Decentralized cloud computing is a transformative approach to infrastructure that provides scalable, secure, and cost-effective solutions for data storage and application deployment. Unlike traditional centralized systems, it leverages a peer-to-peer network powered by blockchain technology, ensuring enhanced privacy, data integrity, and resistance to censorship.
In the Nette ecosystem, decentralized cloud computing underpins the development and deployment of innovative services. It enables users, developers, and businesses to access a global network of resources—such as storage, servers, and applications—on demand. These resources are provisioned with minimal provider oversight, offering unparalleled flexibility and control.
Key Features of Decentralized Cloud Computing in Nette:
- Scalability and Elasticity: Users can adjust resources dynamically to meet their needs without overcommitting costs.
- Cost Efficiency: Pay-as-you-go models replace traditional blanket pricing, ensuring optimized spending for varying workloads.
- Enhanced Security and Data Integrity: Blockchain-based storage ensures decentralized encryption and immutability, reducing the risks of hacking and unauthorized monitoring.
- Censorship Resistance: Decentralized networks store data across multiple nodes, ensuring continuous accessibility even in restrictive environments.
By embracing decentralized cloud computing, the Nette ecosystem leads the way in redefining how data is stored, accessed, and secured, fostering innovation and resilience in digital services.
Nette Ecosystem Wallet: Secure, Flexible, and Inclusive
The Nette ecosystem wallet is a versatile digital wallet designed to manage tokens within the Nette ecosystem and beyond. It is the cornerstone of financial interactions in the Nette ecosystem, providing users with seamless access to their digital assets and enabling quick, secure transactions.
Key Features of the Nette Wallet
- Dual Transaction Modes
- Inside the Ecosystem: Transfers within the Nette ecosystem are highly convenient. In addition to using traditional wallet addresses (starting with "NE"), users can transfer tokens simply by entering the recipient's registered email address, ensuring ease of use and accessibility for all users.
- Outside the Ecosystem: Tokens can also be transferred to external wallets by using their NE-format wallet addresses, allowing users to integrate their digital assets with other blockchain networks.
- User-Centric Design
The wallet's intuitive interface simplifies asset management for users of all experience levels. From tracking balances to initiating transfers, every feature is designed to maximize usability.
- Enhanced Security
Security is a top priority in the Nette ecosystem wallet. Features such as two-factor authentication (2FA), end-to-end encryption, and secure private key storage ensure the safety of users' assets during all transactions.
- Integrated Ecosystem Services
The wallet seamlessly connects with other Nette services, including staking, crowdfunding, and marketplace activities, making it a one-stop solution for ecosystem engagement.
- Global Accessibility
With support for cross-border transactions and multiple transfer methods, the wallet ensures that users can interact with the Nette ecosystem wherever they are in the world.
The Nette ecosystem wallet bridges the gap between user-friendly design and robust functionality. Whether transferring tokens to another ecosystem user via email or sending assets to external blockchain wallets, the wallet ensures a smooth, secure, and efficient experience. By empowering users with innovative features and unmatched flexibility, the Nette ecosystem wallet represents the future of digital asset management in a decentralized world.
Interoperability in the Nette Ecosystem:
Bridging Blockchains for Seamless Connectivity
The Nette ecosystem prioritizes interoperability, addressing one of the most critical challenges in the blockchain industry: the ability to connect and exchange data between fragmented blockchain networks. This feature ensures seamless interactions across different chains, unlocking the true potential of decentralized ecosystems.
The Need for Interoperability
While blockchains excel at enabling digital currencies, smart contracts, and industry-specific applications like supply chain tracking and healthcare, most operate in silos. This lack of connectivity restricts functionality and forces users to work within isolated systems. For instance, token transfers and smart contract execution are typically confined to a single blockchain, creating barriers for broader economic activity.
How Interoperability Works
Interoperability relies on the ability of blockchains to freely exchange data and execute transactions across networks. This is achieved through solutions that enable:
- Cross-Chain Data Sharing: Ensuring that transactions recorded on one blockchain can be verified and interacted with on another.
- Trustless Exchanges: Mechanisms like atomic swaps allow users to exchange digital assets securely and without reliance on intermediaries, although these do not involve transferring tokens across blockchains.
- Routing Protocols: These enable the destruction of tokens on the source blockchain and their recreation on the destination blockchain, effectively transferring value between chains.
Router Protocol in the Nette Ecosystem
To enhance interoperability, the Nette ecosystem integrates with the Router Protocol, a cross-chain interoperability layer that connects multiple blockchains.
- Supported Networks
The Router Protocol infrastructure is live on nine major EVM-compatible chains, including Ethereum, Binance Smart Chain (BSC), Fantom, Polygon, Optimism, Arbitrum, Avalanche, Aurora, and Kava. - Key Offerings
- Voyager DApp: A flagship application enabling cross-chain swaps of any asset to any asset.
- CrossTalk: A communication layer for cross-chain smart contracts, empowering advanced use cases like lending and staking across blockchains.
Benefits of Nette Ecosystem Interoperability
- Enhanced Flexibility: Users can seamlessly interact with multiple blockchains, avoiding the limitations of isolated systems.
- Broader Economic Potential: The routing protocol expands economic activity by facilitating token and data transfers between chains.
- Future-Proof Solutions: By integrating advanced interoperability technologies, the Nette ecosystem remains at the forefront of decentralized innovation.
The Nette ecosystem's commitment to interoperability ensures users benefit from a connected, versatile blockchain environment, paving the way for greater adoption and functionality.
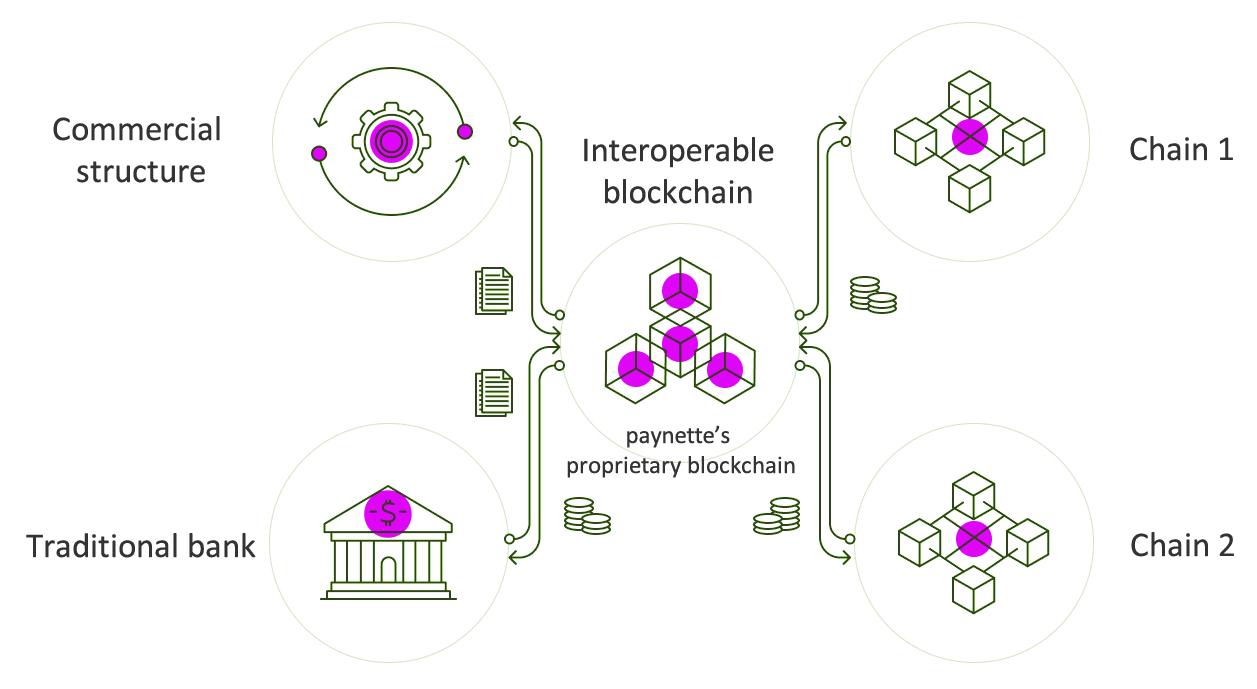
key features
The Nette Ecosystem offers a decentralized Payment Aggregator Protocol (dPAP) designed for seamless and efficient payment transactions. Users—whether individuals, businesses, or financial service providers—can easily interact with the ecosystem through web and mobile applications. The dPAP is adaptable and can integrate with various systems, including crypto wallets, accounting software, financial data platforms, e-commerce, and supply chain management tools.
The Nette Ecosystem's dPAP includes the following key features:
- Real-time Payment Processing: Experience near-instantaneous payment processing without the need for intermediaries. Transactions are conducted 24/7, ensuring uninterrupted service and high operational efficiency.
- Automatic Recording and Immutable Ledger: All transaction data, including details related to currency conversions and payment documentation, are automatically verified, time-stamped, and recorded in an immutable ledger. This ensures transparency, data integrity, and an unalterable record of all transactions.
- Comprehensive Payment Tracking: The ecosystem's distributed ledger technology allows users to monitor transactions in real-time and trace their full lifecycle from initiation to completion.
- Full Audit Trail for Payment Documents: The dPAP securely records and stores data about payment-related documents such as invoices, receipts, and letters of credit. This includes detailed records of document creation, modifications, viewing, and sharing for enhanced accountability.
- Multi-currency Support: Facilitates seamless transactions in both crypto and fiat currencies, empowering users to operate in a diverse and dynamic financial environment.
- QR Code-Based Payments: Simplifies transactions through quick and accurate QR code scanning, minimizing the potential for human error while ensuring encrypted wallet addresses and payment details are securely transmitted.
- NFC-Based Payments: Enables fast, secure data transfer for payments between NFC-enabled devices, offering convenience and improved user experience in close-proximity transactions.
- Biometric Authentication: Utilizes cutting-edge biometric technology, such as fingerprint, palm, and corneal scanning, for secure user identification and payment authorization.
- Smart Contract Automation: The ecosystem incorporates self-executing smart contracts that automate payment processes based on predefined conditions, enhancing reliability and trust for all parties involved (e.g., automatic payment upon product delivery).
- Electronic Signature Verification: Each participant in the dPAP has a unique digital signature, allowing for the electronic signing of transactions and providing verifiable proof of ownership.
- Cryptographic Hashing: Every data block in the network is assigned a unique cryptographic hash. Any modification to transaction data triggers changes in subsequent block hashes, alerting users to potential tampering and maintaining data integrity.
- Enhanced Security Protocols: User data is protected through multi-factor authentication, nested encryption, advanced fraud detection algorithms, and more, ensuring the highest level of security for all financial interactions.
- Automated KYC/AML Compliance: The dPAP incorporates automated Know Your Customer (KYC) and Anti-Money Laundering (AML) verification processes. These ensure real-time customer authentication, an immutable audit trail for all changes to user information, and adherence to global regulatory standards.
ownership and copyright
legal owner:
- the nette ecosystem.
dubai, united arab emirates.

CEO speech:
I am thrilled to introduce you to Tradenette, a company built on innovation, dedication, and a vision for a better future. As the CEO, I am honored to share our journey, our mission, and our exciting plans for the future through this whitepaper.
Our Vision and Mission
At Tradenette, we believe in harnessing the power of technology to create seamless, efficient, and secure trading solutions. Our mission is to democratize access to financial markets, empowering individuals and businesses alike to achieve their financial goals with confidence. We strive to break down barriers and provide cutting-edge tools that make trading accessible to everyone, regardless of their background or experience. By leveraging automation and precision cooling technologies, we aim to deliver a platform that sets new standards in performance and reliability.
Our Journey
Our journey began with a simple yet powerful idea: to transform the trading landscape by leveraging the latest advancements in technology. Over the past few years, we have built a robust platform that integrates automation, precision cooling, and state-of-the-art security features. This journey has not been without its challenges, but our dedicated team of engineers, analysts, and innovators has worked tirelessly to overcome them. Together, we have created a platform that is not only powerful but also user-friendly, providing traders with the tools they need to succeed in an increasingly competitive market.
Innovation at Our Core
Innovation is at the heart of everything we do. From our intuitive user interface to our sophisticated trading algorithms, every aspect of Tradenette has been designed with the user in mind. Our research and development team is constantly exploring new technologies and methodologies to enhance our platform. We are particularly proud of our precision cooling technology, which ensures that our systems operate at peak performance even under the most demanding conditions. This commitment to innovation allows us to deliver a seamless trading experience, with unparalleled speed, reliability, and security.
Community and Collaboration
We understand that our success is deeply intertwined with the success of our community. That's why we are committed to fostering a collaborative environment where ideas can flourish, and innovation can thrive. We value the feedback and insights of our users and are dedicated to building a platform that meets your needs and exceeds your expectations. Our community is our greatest asset, and we believe that by working together, we can achieve great things. Whether you are a seasoned trader or a newcomer to the financial markets, we welcome you to join us on this exciting journey.
Looking Ahead
As we look to the future, we are excited about the endless possibilities that lie ahead. Our upcoming Initial Coin Offering (ICO) marks a significant milestone in our journey, providing us with the resources to further develop our platform and expand our reach. The funds raised through the ICO will be used to enhance our technology, improve our infrastructure, and broaden our range of services. We are also exploring new partnerships and collaborations that will enable us to bring even more value to our users. Our goal is to make Tradenette the go-to platform for traders around the world, offering the best tools, the best technology, and the best user experience. In conclusion, I want to thank each and every one of you for being a part of the Tradenette community. Your trust and support are the driving forces behind our success. Together, we can build a future where trading is accessible, efficient, and rewarding for all. We are committed to pushing the boundaries of what is possible and delivering a platform that empowers you to achieve your financial goals.
Warm regards,
emma lawson
CEO deputy of Nette Ecosystem
our subsidiary trademarks:
- tradenette - https://tradenette.com/
- paynette - https://paynette.com/
- coinette - https://coinette.net/
- nettescan - https://nettescan.com/
copyright:
Copyright, a type of intellectual property law, safeguards original works of authorship such as poetry, sample books, movies, songs,
computer software, algorithms, and architecture, as well as literary, theatrical, musical, and creative works.
All contents (of any kind), trademarks, logos, and other materials related to the Nette Project and its subassemblies belong to Nette Ecosystem LLC and are protected by trademarks, copyrights, and other intellectual property laws.
© 2025 The Nette Ecosystem. All rights reserved.
Copyright is applicable under our
subsidiary trademarks.
the coinette™
The QUI (pronounced /koi/) or Coinette™ (pronounced /koinet/) is a utility token (a type of cryptographic token) to support the entire Nette ecosystem. The Coinette token (QUI) will initially be launched on the Tron blockchain with the TRC20 standard. During an initial exchange offering (IEO) scheduled for February 2024, it will be released with up to 300 million QUI tokens (about 139 million USDT).
All proceeds from the sale of the QUI token will be converted to one of the stable coins (preferably Tether USDT) and stored in the TRON network. As long as Coinette needs support, this process will continue.
utility token
The utility token has emerged as a vital tool for raising capital and financing crypto projects. While the traditional investment market usually lacks diversity and utility, the cryptocurrency market provides it all to investors and businesses. However, if you are new to the world of crypto investing, it is essential to understand the basic concepts of the subject to avoid future pitfalls. Some role of utility tokens are:
- Access to services: The main role of utility tokens is to grant access to certain services or products on the blockchain platform. These tokens act as a form of digital currency that users can use to make payments and access functions offered by the platform.
- Token creation: Utility tokens are created through Initial Coin Offerings (ICOs) or Token Generation Events (TGEs). During these events, users can purchase utility tokens using other digital currencies, such as Bitcoin, Ethereum, Tronix, or Tether.
- Smart contracts: Many utility tokens work on blockchain platforms that support smart contracts. These contracts define the terms and conditions of utility tokens and ensure that they are used for their intended purpose.
- Limited functionality: Unlike security tokens, utility tokens typically do not represent ownership in a company or share in profits. Instead, their value is tied to their functionality on the platform, and they are often designed to be used solely to access certain services.
- Token exchange: Utility tokens can be traded on digital currency exchanges. The value of these tokens may fluctuate based on supply and demand dynamics, as well as the success and popularity of the associated platform.
- Redeemable: Users can use utility tokens to pay for services or products on the platform. In some cases, holding a certain amount of tokens may also bring additional benefits or privileges.
- Community participation: Some blockchain projects involve utility token holders in decision-making processes. Token holders may have voting rights regarding platform development, upgrades, or other governance-related matters.
- Ecosystem growth: Functional tokens play a role in promoting the growth of the project ecosystem by encouraging users to actively participate. This can contribute to the overall success and sustainability of the platform.
why tron network?
Tron is a decentralized, open-source blockchain platform that has its own native cryptocurrency called Tronix, or TRX. Tron can run smart contracts, and it can be used to build decentralized apps. It has a lot of similarities with Ethereum, as it was an Ethereum-based token before building its own blockchain. Tron aims to help share digital content more economically by hosting a worldwide entertainment system. The software developers use the Solidity programming language to host decentralized entertainment platforms on the Tron network.
The TRON Virtual Machine (TVM) is responsible for maintaining the Tron ecosystem, which is very similar to the Ethereum Virtual Machine. This machine helps in providing an effective blockchain system. The TVM helps in executing smart contracts. It has a three-layer architecture that includes the storage, core, and application layers. The consensus mechanism used by Tron is delegated proof-of-stake. Using this technique, the users use their currencies to vote for the delegates, who take important decisions to operate the entire network. Super representatives keep track of the transaction history and validate transactions. They receive TRX coins in exchange for their services. Every three seconds, the blockchain acquires a new block. Those who add blocks get a reward of 32 TRX coins for their services. Additionally, smart contracts for Tron are written in Solidity and other advanced languages.
TRC20 token
The TRC-20 token standard is an open-source, decentralized, peer-to-peer protocol created to solve compatibility issues between different tokens and wallets. The TRC-20 token protocol enables the creation and trading of tokens on the TRON network. The protocol also enables the creation of smart contracts and decentralized applications on the TRON network. The protocol is designed to be scalable and allow the creation of high-performance DApps. The TRC-20 protocol is also compatible with the Ethereum network, allowing for the creation of on-chain applications.

- name: coinette™
- legal holder: Nette Ecosystem LLC
- goal: funding for projects through crowdfunding and a dedicated crypto token sale
Projects that need to sell Coinette for development:- primary, paynette™
- auxiliary, tradenette™
- abbreviation: QUI
- symbol:
- icon:

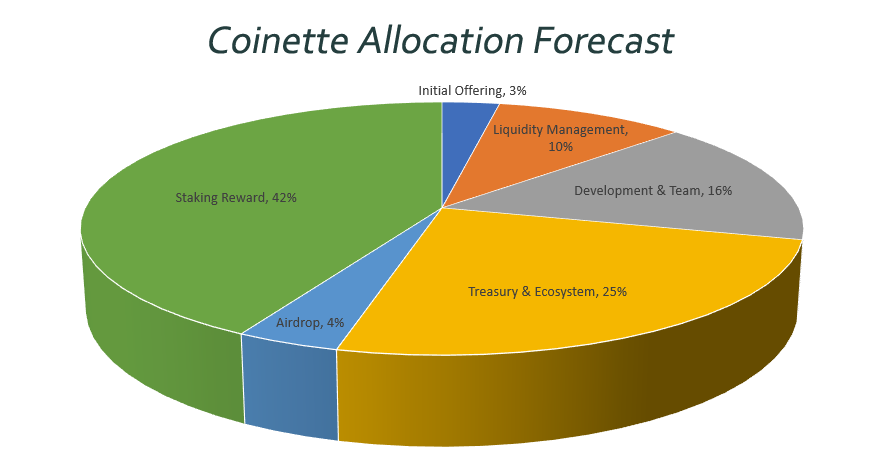
milestones
Milestones are specific results or goals that we aim for as part of our business strategy. That is, short-term, measurable goals to achieve our bigger goals. Good business milestones should include the following:
- Measurable results
- Expected completion date
- Clear accountability
- Budget allocation
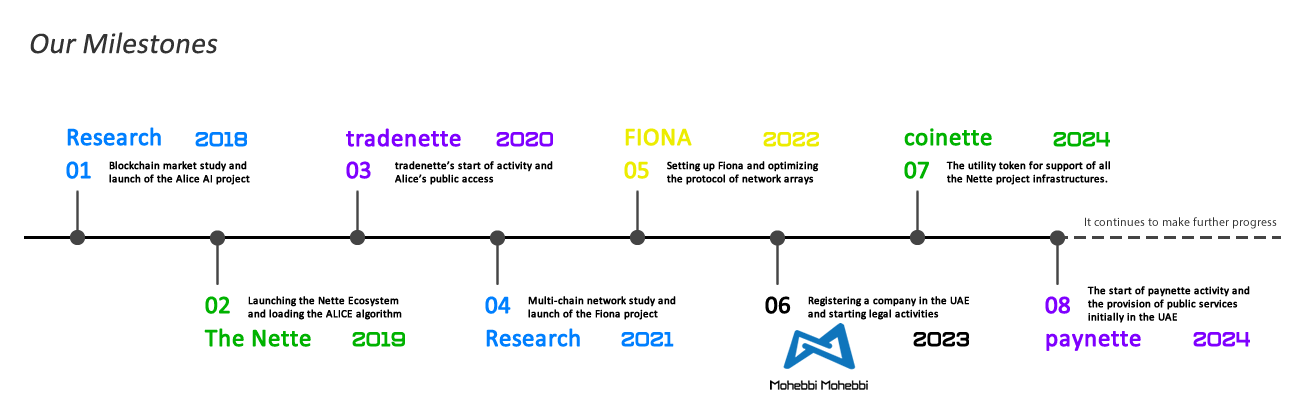
customer 360°
Behind the scenes of most companies are people who never meet or have the opportunity to meet buyers; instead, customer service staff are in direct contact with buyers and hear their opinions and expectations. Customer loyalty is highly dependent on their experience with the customer service department. For this reason, many companies work hard to increase the level of customer satisfaction.
Therefore, customer service is the first priority in our organizational and business strategies. A dynamic and interactive web application that provides easier and more accessible support for all customers and enables effective 24/7 communication and the artificial intelligence used in our infrastructure allows for detailed analysis of defects and weaknesses to enable continuous improvement.
There are many reasons why businesses should invest in customer service. The following are just some of the main benefits of a well-implemented customer service program from our perspective:
- Customer retention: The first and most obvious benefit of having a customer care service plan is keeping customers happy. This means listening to concerns, empathizing with them, and facilitating issues related to product availability, payment, returns, and technical support. Showing that a company cares keeps customers loyal.
- Employee retention: Customer care service isn't just for customers. It also helps retain employees with the company. When customers are happy, employees are happy too. People tend to work in an environment that cares about their customers.
- Troubleshooting and Solving: Businesses need to address their customers' problems. But companies that take a proactive approach do better. This means that it is important to communicate with customers before any problems arise. This shows that the company cares and goes out of its way to ensure a smooth customer experience.
- Referrals: Consumers who have a good experience often pass that information on to others, whether through word of mouth to people they know, customer reviews, or social media. This often helps businesses generate new sales.
- Strengthens the brand: Businesses that show consumers that they care through customer service help increase their brand equity. This also leads to more referrals and, as a result, increased sales.
- Strengthens the brand: Businesses that show consumers that they care through customer service help increase their brand equity. This also leads to more referrals and, as a result, increased sales.
- Corporate culture: Customer service allows businesses to streamline their workflows and promote collaboration between different teams. This includes communication between agents and managers, technical engineers, and production teams. All of this is to help companies achieve their goals of attracting and retaining customers and increasing sales revenue.
- Competitive Advantage: Having a good customer service base differentiates the company from its competitors. This increases the reputation of the business as well as its brand value by showing consumers and competitors that the business values the relationships it has with new and existing customers.
accuracy of whitepaper content: Although we aim to provide accurate, correct, and clear content, it may not always be completely accurate and may also contain technical errors or typographical errors. In an effort to provide complete and accurate information, it may be changed or updated from time to time without notice, including about our policies, products, and services. Accordingly, you should review and verify all information before relying on it, and it is your responsibility not to make decisions based solely on the information provided. We will not be responsible for any decisions made by you. Information provided by third parties is for informational purposes only, and we make no guarantees as to its accuracy. Links to third-party content may be provided for convenience but are not controlled by us. YOU ACKNOWLEDGE AND AGREE THAT WE ARE NOT RESPONSIBLE FOR ANY ASPECT OF THE INFORMATION, CONTENT, OR SERVICES IN THIRD PARTY CONTENT OR THIRD PARTY SITES LINKED TO THIS CONTENT.
forward-looking statements: This whitepaper contains certain statements about the future of our business based on the beliefs of the development team at paynette, as well as the engineering plans, business plans, and customer-centric assumptions made by the tradenette architecture team. These statements, by their nature, are subject to various changes and uncertainties and may include estimates and assumptions that are affected by external factors beyond our control and prediction. Accordingly, these factors could cause actual results or outcomes to differ materially from those expressed in these statements. We undertake no obligation to update any forward-looking statements that reflect particular events or circumstances after the release of this content.